




Price: $17.15
(as of Sep 26, 2024 18:27:34 UTC – Details)

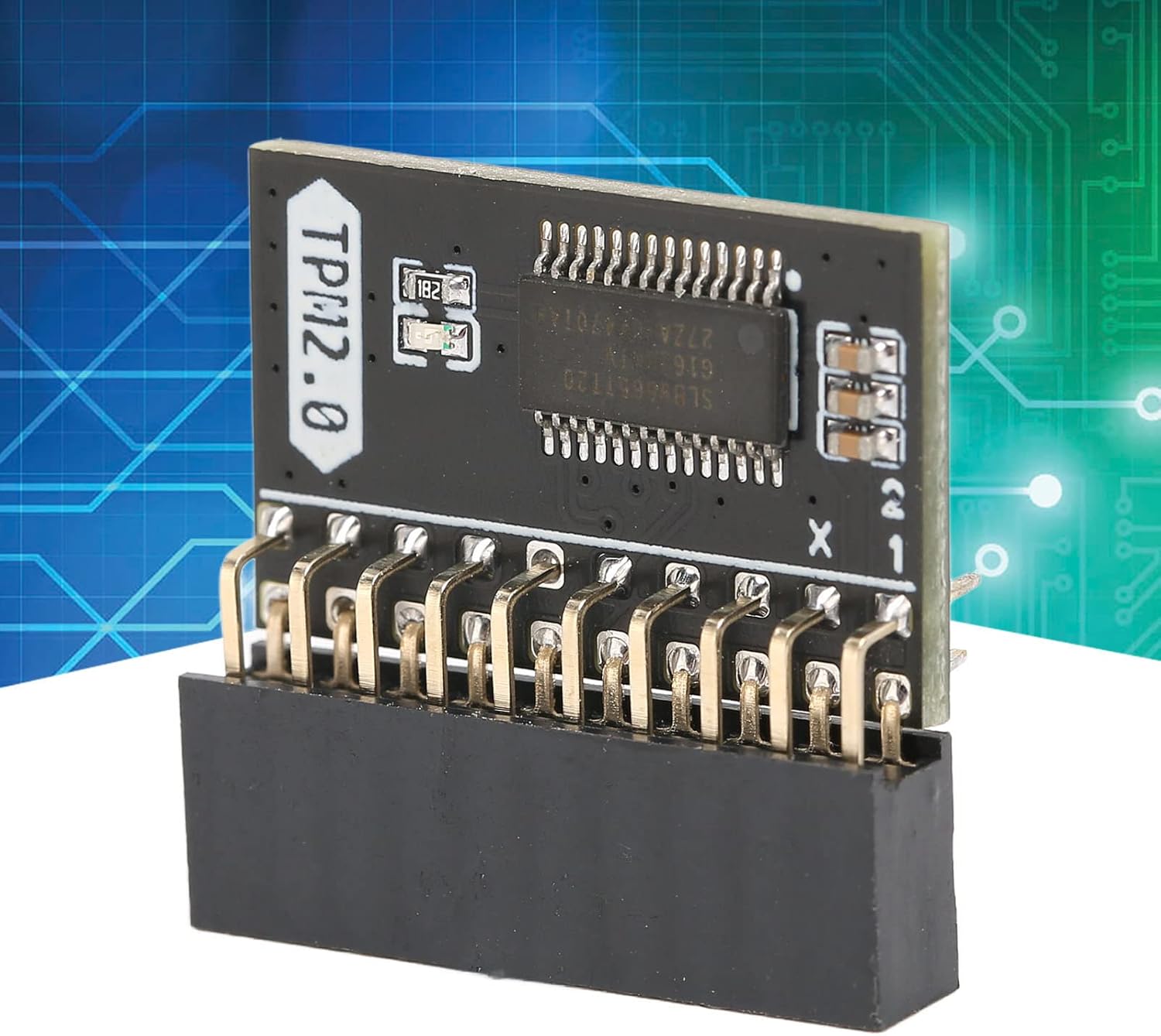
1. Standalone Crypto Processor: The TPM is a standalone crypto processor connected to a daughter board connected to the motherboard. The TPM securely stores encryption keys that can be created using encryption software.
2. Prevent Access: Without this key, the content on the user’s PC remains encrypted and protected from unauthorized access.
3. Replacement: A replacement TPM can replace your original damaged, unusable or underperforming TPM, which helps repair your device and make it work. The function is the same as the original.
4. Compatibility: TPM chip is better compatible with DDR4 memory module of motherboard, built in support memory type higher than DDR3! Supported states may vary by motherboard specification.
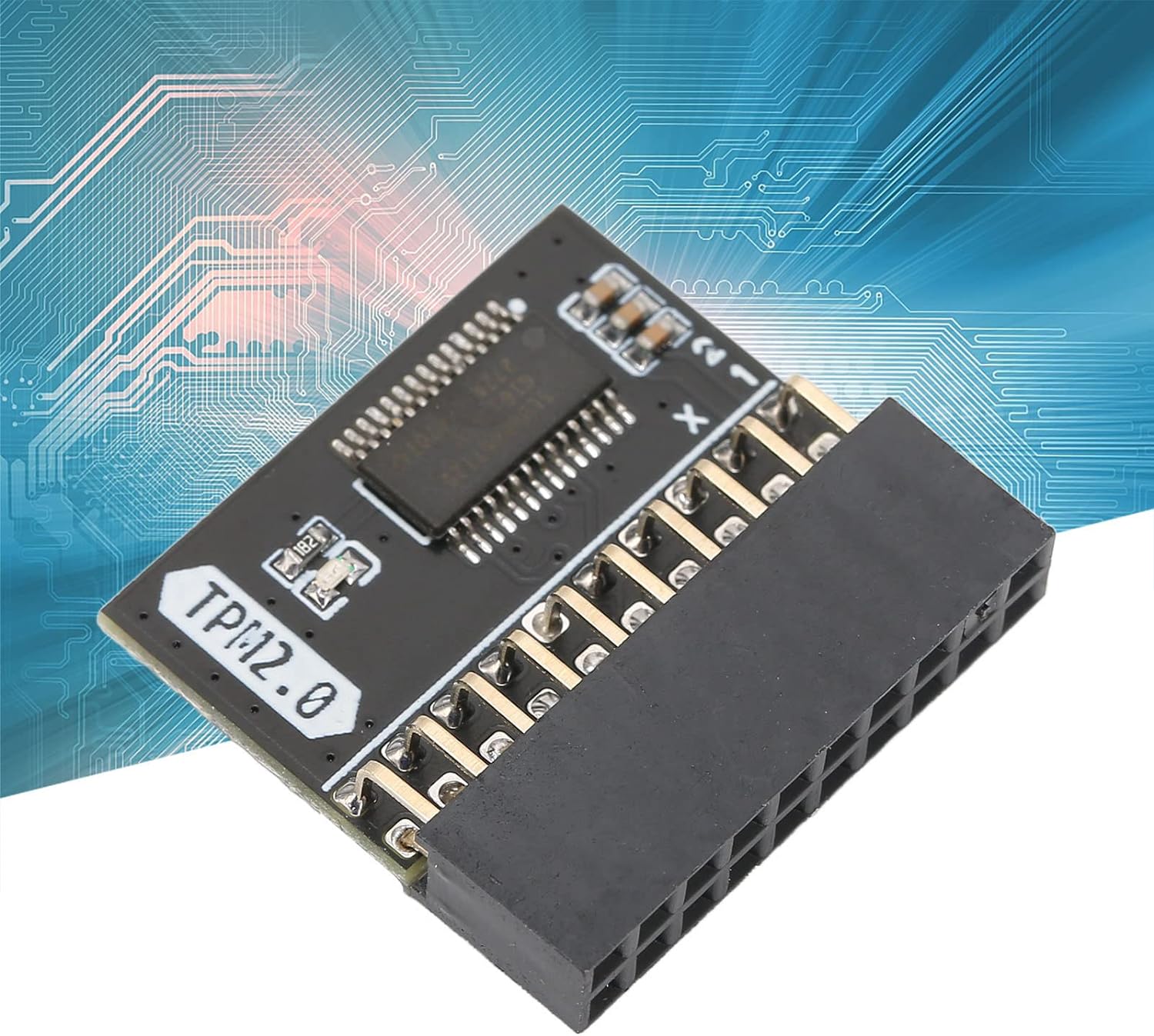
5. Scope of Application: TPM 2.0 module 2.54mm pitch, 2x10P, 20 1 pin security module for Gigabyte, for .
Specification:
Item Type: TPM 2.0 Encryption Security Module
Material:PCB
Compatible Device: PC
Pin Definition: 20Pin
TPM Version: TPM 2.0
How to Use:
Take out the product and use it
PackageList:
1 xTPM 2.0 Encryption Security Module
Notice:
Note that not all for gigabyte boards support this TPM module.
COMPATIBILITY: TPM chip is better compatible with DDR4 memory module of motherboard, built in support memory type higher than DDR3! Supported states may vary by motherboard specification.
Standalone Crypto Processor: The TPM is a standalone crypto processor connected to a daughter board connected to the motherboard. The TPM securely stores encryption keys that can be created using encryption software.
Replacement: A replacement TPM can replace your original damaged, unusable or underperforming TPM, which helps repair your device and make it work. The function is the same as the original.
Replacement: A replacement TPM can replace your original damaged, unusable or underperforming TPM, which helps repair your device and make it work. The function is the same as the original.
Standalone Crypto Processor: The TPM is a standalone crypto processor connected to a daughter board connected to the motherboard. The TPM securely stores encryption keys that can be created using encryption software.
This post is exclusively published on eduexpertisehub.com

